For months now, someone has been hacking into the email and social media accounts used by Polish ministers, MPs, journalists and soldiers. Semi-nude photos of councillors, fake adverts on websites used by sex workers and news about a radioactive cloud that originated over Lithuania are being disseminated online. What do these attacks have in common?
The evidence, as VSquare has established, is leading to a hacker group known as “Ghostwriters”, which is pursuing Russia’s goals.
“Thousands of accounts have so far been seized. It’s a ticking bomb,” our source in the Polish secret services has said.
Disinformation campaigns that use hacked accounts are repeated every few weeks in Poland but attract only short-lived media attention. Although unidentified hackers managed to seize the accounts of the Speaker of the Sejm, government members, a group of MPs (including a member of the secret services committee) as well as local government officials, Polish politicians still do not consider the threat as serious.
1.
The hacker puts out bait
It starts with a phishing attack. The hackers fabricate social media posts or use other electronic services to steal a person’s login and password. An effective phishing attack allows hackers to take over your email account, including a list of contacts, and if the inbox is connected to social media or the same password is used in several accounts, the door opens to use other accounts and access the content stored on the individual’s phone. Twitter and Facebook accounts seized in a phishing attack are then used in a disinformation campaign.
Shocking tweets allegedly posted by politicians, although they are a spectacular aspect of the campaign, are only the tip of the iceberg. The phishing attack may use fake websites that claim to be managed by state institutions, hacked and real news websites or official websites of the institutions, as well as correspondence from other hijacked email accounts.
It is a long-term, organised and wide-ranging disinformation operation that requires a lot of effort and resources. Its exact goals are still unclear. We have learned, however, that the group behind the series of attacks may have already obtained a huge amount of sensitive data about key people in Poland.
“The operation of obtaining ‘kompromats’ on MPs, journalists and analysts has been underway for months. The email addresses targeted by phishing attacks are not random. Members of the politicians’ families are also targetted,” says our source in secret services.
These addresses are not public. This proves that individuals who fall victim to attacks have been carefully selected and researched before the operation is launched. “Therefore we are talking about operations that might include profiling, blackmail, espionage and manipulation,” reveals another of our sources.
We decided to take a closer look at this operation. Who is behind it? What does this group aim to achieve?
2.
Hacking attack leaves behind a trail of evidence
“Huge scandal! Lithuanian special services accuse Poland of training extremists!”, “Sexual harassment at the Ministry of National Defence. The fallout of the scandal has reached President Duda, the head of Lithuanian diplomacy and American generals”, “The National Atomic Energy Agency is sounding an alarm! Radiological hazard in Poland”.
These are just a few of the headlines that have been published in recent months on Polish websites and social media accounts hacked by cybercriminals.
On March 17, a fake article about a radioactive cloud that originated in Lithuania is published on the website of the National Atomic Energy Agency (PAA), sounding a dire warning that Poland is facing an ecological disaster. The news published on PAA website is based on a report published by the Lithuanian Nuclear Power Safety Inspectorate (VATESI). The cybersecurity portal niebezpiecznik.pl reported that the fabricated report was published on a fake website – its address had an “l” replaced by an “i”: vatesl.lt.
Five minutes after vatestl.lt reports a ‘radioactive incident’ in Lithuania, hackers publish a fake announcement with a warning about a radioactive cloud on the PAA website. After another several dozen minutes, similar information is published on zdrowie.gov.pl, the official website of the Polish Ministry of Health, this time the fabricated text focuses on the symptoms of radiation sickness.
Then such fake-news media reports go global – hackers re-tweet them using the account of a right-wing journalist and a Russia expert Marek Budzisz. The account, which the hackers control for a few hours, shares the tweet dozens of times, tagging, among others, Poland’s Prime Minister Mateusz Morawiecki. It also links to the hacked pages of PAA and the Ministry of Health and their copies in web archives.
The fake story is also shared from the accounts of two local PiS activists: Mirosław Walicki – the starost of Garwolin and Andrzej Rochmiński, head of local party structures in Zielona Góra. The hackers expect the information will quickly be removed from the official PAA website, so they use the Facebook profiles of councillors to post entries that link to the archived version of the warning on PAA website. As a result, information about the radioactive cloud is still available to those who follow the councillors’ profiles.
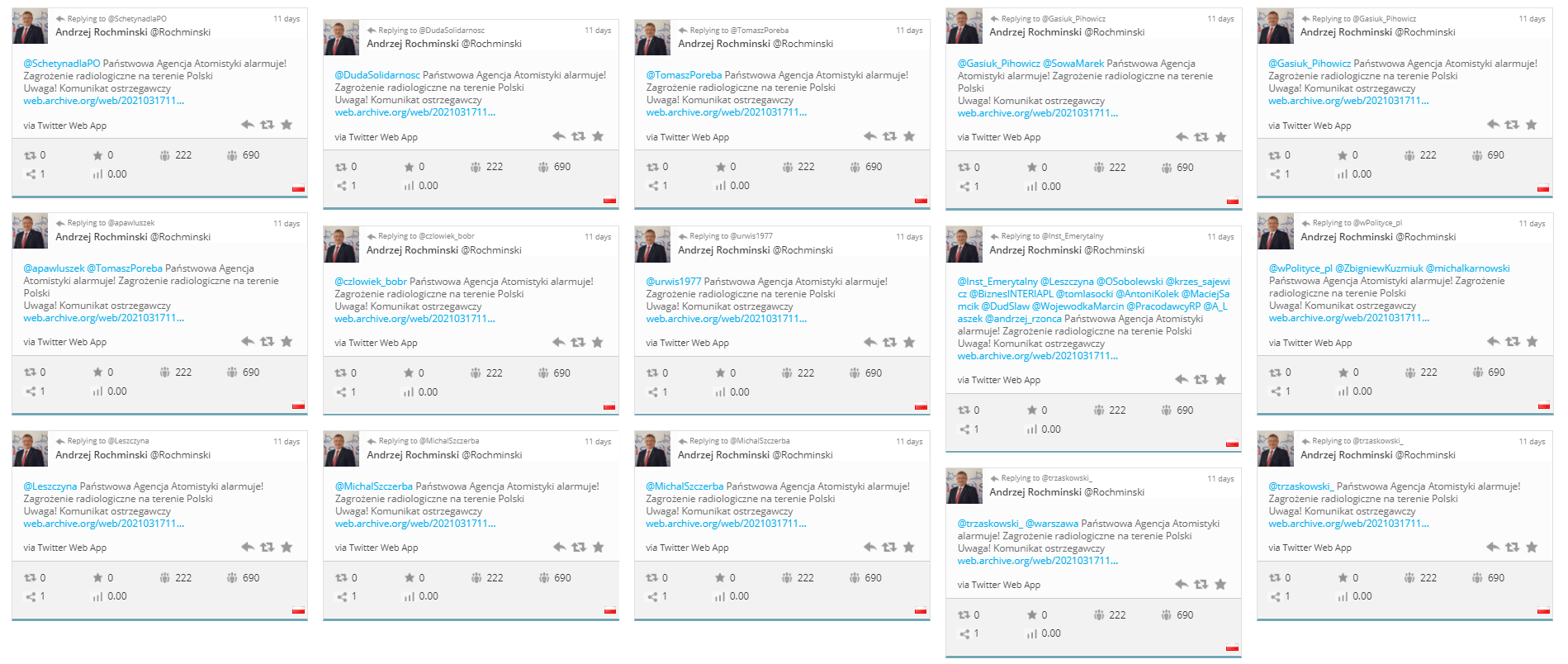
Identical posts from the hijacked profile of Andrzej Rochmiński, local PiS activist.
As reported by niebezpiecznik.pl the entire PAA content management system (CMS), or even a company that supports government administration institutions, has probably been hacked. That day, Poland’s National Atomic Energy Agency labels this as fake news. A few hours later Marek Budzisz informs that he has regained control of his Twitter account.
Konkret24, a fact-checking portal, has reported that the attack coincided with the talks of the Polish and French governments about the construction of a nuclear power plant in Poland.
Our sources indicate that Budzisz and Walicki’s email accounts had previously been among addresses hacked as part of an organised phishing operation during which cybercriminals seized the email accounts of MPs and members of the government.
We have also found out that the fake story that ran on a fabricated website was a manipulation of an authentic VATESTI announcement about public consultations on a radioactive waste storage site, which had run on local websites just hours earlier. The website vatesl.lt was set up on the same day, several hours before the attack.
3.
Hacker targets in the military
The seemingly trivial, malicious attacks on politicians, veiled as an attempt to provoke a moral scandal, also have another concealed purpose.
On 25 February 2021 cybercriminals launch another attack – they use the websites of the Speaker of the Sejm, Elżbieta Witek, the right-wing weekly Tygodnik Solidarność website tysol.pl, the account of the deputy minister of science and a PiS senator, and private photos of a NATO soldier. What does an attack involve?
As their first move, cybercriminals gain access to unpublished photos of a woman involved in military missions. They most likely hack her email account or private Facebook profile.
Then, a fabricated advert is published on the website used by sex workers: “My talent has already touched many hearts and will be remembered by many world leaders, VIPs and generals for a long time”. The advert is signed and includes photos stolen from the soldier’s Facebook profile (profile photo and snaps from military missions). There is also a photo taken during a mission in Kuwait, where she was photographed with Polish President Andrzej Duda.
A screenshot of the advert is posted on the Twitter account of the deputy minister of science Włodzimierz Bernacki, which had been seized by hackers, and a fake Twitter account of PiS senator Marek Martynowski. The first account comments on the sex advert, which disseminates it further, the second account spams opinion-making profiles, making a visible impression.
Before the story goes viral on social media, something else happens – a screenshot of a fabricated post shared from the account of the deputy minister of science ends up on the parliamentary website of Elżbieta Witek. It is labelled as: “Regarding a proposal by the secretary of state at the Ministry of Science and Education, Włodzimierz Bernacki, the National Defence Committee is currently investigating a prostitution ring in the Polish Army and a defamation case that includes insulting the President.”
But the hackers go further – they break into a right-wing website tysol.pl and publish a bogus article based on a fabricated entry on Witek’s website. The piece is illustrated with photos of the soldier – this time on a military plane – stolen from her private profile.
The entry also mentions the head of Lithuanian diplomacy, Gabrielius Landsbergis, which clearly proves that the fake is aimed to target not only the Polish audience. The authors of the fabricated piece published on tysol.pl argue that Landsbergis allegedly met, at his request, the second lieutenant during his official visit to Poland in February 2021. The politician, however, allegedly had met the soldier earlier, when he visited Polish pilots at the Lithuanian air base in Šiauliai. The hackers wrap up their fabricated story: “Our sources have confirmed that the Ministry of Defence regularly uses women, particularly officers, to provide escort services for VIPs.”
Fake news prepared in this way is then sent to… Lithuania.
The Lithuanian Ministry of Foreign Affairs quickly deems the reports fraudulent. The editors of tysol.pl discover that their website has fallen victim to a hacking attack and remove the story.
We asked the Chancellery of the Sejm if they knew that the Speaker of the Sejm also had been targetted in a hacking attack? We asked them to explain the entry published on Elżbieta Witek’s website (the site is still under maintenance). Unfortunately, we have not heard from the Sejm’s Information Centre, which has disregarded our requests for details.
When we analyse the public contents of the soldier’s account, our attention is drawn to her wedding photos. The account shows that her partner, most likely a soldier who participated in foreign missions, was part of a special forces unit in western Poland. We call him to ask about the break-in into his partner’s account. He says we have the wrong number and hangs up. Moments later, he changes the content of his Facebook profile – photos with the woman from Bernacki’s tweets are no longer available.
4.
Hacker blackmails an MP
In November 2020, several posts are published on Marcin Duszek’s (PiS) Facebook and Instagram accounts. The fake post suggests the MP is accompanied by a nude assistant. Commentators talk about the revenge of his lover or the young MP’s self-indulgent social life.
Meanwhile, looking at the posts included on Duszek’s social media, the matter no longer seems a scandal on the MP’s morality. It turns out that his account had been hacked long before the photos of the ‘assistant’ were released, or that cybercriminals had hacked it twice. In October, less than a month before the photos of Duszek’s alleged assistant are leaked, his Twitter account posts a link that redirects to an article included on the prawy.pl website: “Poland at the epicentre of the fight. NATO is getting ready for a great war with Russia”. At the same time, a few minutes apart, an identical entry is published on the accounts of two PiS politicians, Joanna Borowiak and Andrzej Melak (the latter account will also be available in the popular, closed Facebook group that includes supporters of Prime Minister Mateusz Morawiecki).
The article they share is a fabricated story. The Konkret24 website, which described hacking attacks on PiS politicians, has reported: “A crafted text from the space24.pl website, under a changed headline, was published on the local news website Obserwator Nadodrzański ono24.info and on prawy.pl website.” The changes included a new headline and three extra paragraphs – they talked about NATO’s plans to increase the size of the alliance’s troops in Poland, Lithuania and Latvia.
The VSquare team has learned that most of the hacked emails so far originated in private accounts, mainly in the wp.pl domain, but also on interia.pl and onet.pl (popular domains among Polish users).
MP Duszek also spoke about the wp.pl mail accounts in the Polska The Times daily: “We already know that at the beginning of October some of our email accounts on Wirtualna Polska (wp.) were hacked. On October 6, my mail was also hacked and a strange, encrypted message was placed there. After about a month, I got another message about blackmail and a possible leak of materials that would compromise me if I fail to follow the blackmailer’s instructions. This message has automatically disappeared from my inbox. I did not take it seriously and considered it a stupid joke. This collection of curiosities and fake news, which included content stolen from a private exchange, began to be suddenly published on our profiles as if someone suddenly had gained access to all our accounts and passwords.”
We have conducted an online search and have found out that email accounts in the wp.pl domain are used by, among others, the female soldier whose photos were stolen, Marek Suski’s parliamentary office, and Robert Pietryszyn, a partner in the PR company R4S – all these accounts were used in attacks in January and February 2021.
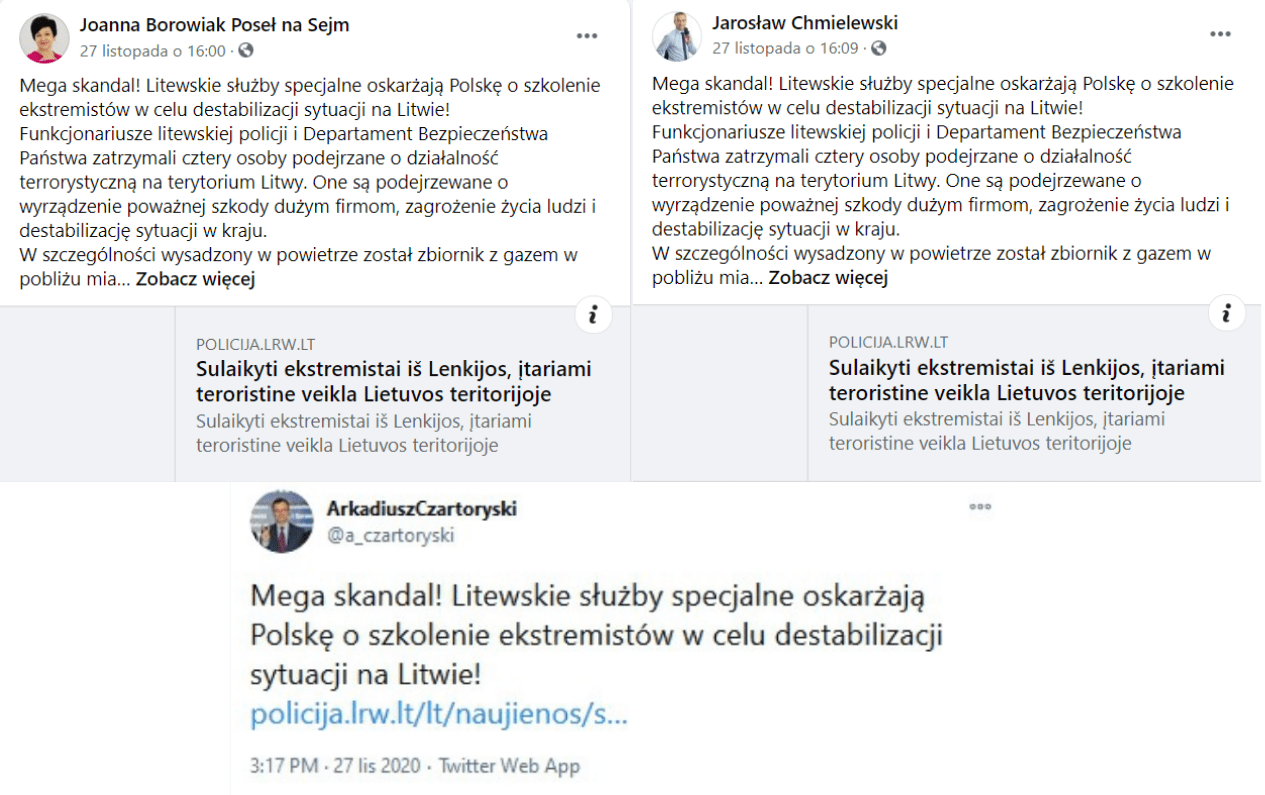
Fake news aimed to undermine Polish-Lithuanian relations are posted on the accounts of PiS MPs.
A month after the first anti-NATO tweets were published on the hacked Twitter of MP Duszek, unknown cybercriminals posted private photos of his partner on Duszek’s Instagram feed. A few days later, fake news aimed to undermine Polish-Lithuanian relations are posted on the accounts of PiS MPs – this time, the hackers use the Facebook accounts of Jarosław Chmielewski, Joanna Borowiak and Arkadiusz Czartoryski and a fake website of the Lithuanian police, which reports that terrorists trained in Poland have allegedly been arrested in Lithuania.
5.
Ghost hacker attacks NATO
The same websites that hackers use in the first cyberattack that included Duszek’s profile (by posting fake news about war preparations), had already been hacked and used in similar, earlier attacks. In April 2020, shortly before the presidential election, prawy.pl and ono24.info news websites had also been used to attack the War Studies Academy (ASzWoj) website. At that time, a fabricated letter allegedly sent by Gen. Ryszard Parfianowicz, aimed at undermining the Polish-American alliance, was published on the Academy’s website. It was followed by a fake article about the letter released by some local (hacked) websites, including ono24.info and prawy.pl (also lewy.pl). FB accounts directly linked to Niezależny Dziennik Polityczny (NDP), widely viewed as spreading Russian propaganda, were used to disseminate the content on social media.
Researchers from the Stanford Internet Observatory managed to show that NDP accounts were the first to share fake content, and thus disseminate the operation among Polish social media websites. This is a strong indication that the attack was driven by the Russian disinformation machine, especially since the material about the general’s alleged letter was distributed on the English-language network by The Duran, a website also regarded as the Kremlin mouthpiece.
FireEye, one of the largest cybercrime tracking companies in America, has linked the attack on the War Studies Academy website (as well as a series of other attacks on news and government websites) with a pro-Russian hacker group dubbed “Ghostwriters”.
FireEye examined disinformation operations in Central and Eastern European information space in 2019 and 2020 aimed at undermining NATO. It was able to link at least a dozen of such attacks to the activities of one group.
“The operations (ongoing since 2017) have primarily targeted audiences in Lithuania, Latvia, and Poland with anti-North Atlantic Treaty Organization (NATO) narratives, often leveraging website compromises or spoofed email accounts to disseminate fabricated content, including falsified correspondence from military officials.”
FireEye has also identified a network of fictional characters – ghost authors who distribute fake content, hence the name of the group “Ghostwriters”: “Based on its use of inauthentic personas posing as locals, journalists, and analysts within the target countries to post articles and op-eds referencing the fabrications as source material to a core set of third-party websites that publish user-generated content” – the report says.
In its study of cyberattacks perpetrated by “Ghostwriters”, FireEye included hacking the War Studies Academy website but also the attack on the right-wing niezalezna.pl website in May 2020. The hackers fabricated content allegedly sent by Katarzyna Gójska, a journalist of the pro-government Gazeta Polska. During the ongoing at the time Defender military exercises in Europe, a translation of Gójska’s fabricated interview with US Gen. Christopher G. Cavoli, the commander of American forces in Europe, was published by The Duran website. What the interview argued? Poland was ill-prepared for the exercises, the Baltic states are affected by equipment shortages, which casts further alliance with the US in doubt. Publications that quote the interview were ‘planted’ on local websites: zary-zagan.pl, regionalna.pl, olsztyn24.com, radioszczecin.pl, but also on right-wing niezalezna.pl, polanddaily.com, telewizjarepublika.pl.
A similar attack takes place in September 2020. An article “Poland and Lithuania call for troops to be sent to Belarus” is planted on the website of the Union of Poles in Belarus, znadniemna.pl, and in Poland Daily. The cyberattack coincides with mass protests of the Belarusian opposition.
The website niezależna.pl claims the attack originated in Riga, Latvia’s capital. The Lithuanian Ministry of Foreign Affairs responded by saying: “False article was published after the hacking of the Polish news portal polanddaily.com, alleging that Lithuanian and Polish foreign ministers offered to send peacekeeping forces to Belarus ‘behind closed doors’. Soon, this false information was also posted on liveleak.com. In order to increase its visibility, a spoofed letter from the Lithuanian Ministry of Foreign Affairs was sent to the editorial board of the US-published weekly The New Yorker, falsely confirming the bilateral conversation between Lithuanian and Polish ministers”.
All evidence, including the focus on NATO, Polish-Lithuanian relations, fabricated articles, hacked news websites, email spoofing, point to typical methods used by “Ghostwriters”. At the same time, a ‘new element’ is used – this time, hackers use the hijacked Twitter account of the editor-in-chief of Gazeta Polska Tomasz Sakiewicz to spread fake news (Sakiewicz has nearly 100,000 followers).
Several days later, there is a successful attempt to ‘hack’ some MPs emails. From then on, fake content is disseminated on Polish social media using hijacked Twitter and FB accounts, which the cybercriminals control after several successful phishing attacks.
6.
Common denominator: the Polish-Lithuanian relations
Our analysis shows great similarities between the actions of “Ghostwriters” in 2019 and 2020 and the ongoing series of cyber attacks on the accounts of Polish politicians. The goals, narratives, but also modus operandi are all similar. The practice used by cybercriminals to distribute online content seems identical – they hack niche media websites and institutional websites, or create fake websites that are close copies of those used by public institutions (as was the case with Lithuania’s Police and the country’s Nuclear Power Safety Inspectorate). An important new channel of attacks includes the use of politicians’ social media accounts (hijacked as a result of phishing), which increase the reach and help disseminate the content without leaving any footprints (as was the case with the cyberattack on the War Studies Academy website, where fake content spread via accounts linked to NDP).
The hacking of email accounts also potentially serves to obtain sensitive information for future operational use.
Although Russia is the beneficiary of the attacks, this does not mean that the attacks are being carried out directly by Russian services. According to our sources, “Ghostwriters” can be a group of intermediaries. The attackers seem to be leaving behind a trail of evidence, the bold cyberattacks utilise large resources but are not particularly sophisticated.
Let’s reiterate – the common denominator of all recent attacks are the Polish-Lithuanian relations. A joint report drawn by the Info Ops Foundation and Lithuania’s organisation Res Publica has concluded that the disinformation campaign aimed at souring the relations between the two countries has been stepped up in recent months: “Russian disinformation operations targeting Polish-Lithuanian relations are not incidental at all (…). In fact, they are elements of well-thought, a sophisticated strategy which aims at achieving long-term goals, also its objectives might seem marginal or irrelevant when analysed separately.”
We asked the Lithuanian Ministry of Foreign Affairs and the Ministry of National Defence about the latest campaign of attacks against Polish-Lithuanian relations: “We assess these attacks as a part of systematic attacks against Western democracies, our NATO allies and Lithuanian-Polish relations. The attacks weren’t only seeking to spread false information, they also were probing the reactions of Lithuanian and Polish authorities, identifying possible weak spots.”
The Lithuanian Ministry of National Defence has said that in 2020 Lithuania was the victim of nine “cyber-enabled information operations” (a higher number than the average annual). “Malign actors constantly put new tactics to the test, but their strategy and main goals remain the same. Cyber-enabled information operations seek to weaken the transatlantic bond, atomize society and weaken its trust in democratic governance. In 2020, operations covered wider geography, in many cases happening simultaneously in Lithuania and Poland. Perpetrators were quick to exploit global and regional issues in their fake stories (COVID-19 pandemic, Defender-2020 military exercise and unrest in Belarus)”.
7.
“The milk has been spilt”
Since October 2020, the Polish media outlets have recorded over a dozen fake news entries on accounts taken over by hackers. The cybercriminals targetted the accounts of at least 18 people.
However, our information shows that thousands of email accounts may have been the target of phishing campaigns. Hackers display a two-pronged approach – they either use an account that has recently been hacked and use it to post fabricated content, or they wait for the right moment and choose not to reveal themselves right away.
That was what happened to PiS politician Marek Suski, whose Twitter profile suddenly posted suggestive photos of a local PiS councillor. According to unofficial sources, the councillor’s private email address had been on a list of hacked accounts much earlier. Suski’s Twitter account was linked to his private mailbox on the wp.pl domain. Did the MP who sits on the parliamentary committee for secret services keep any sensitive data there?
The District Prosecutor’s Office in Grójec is investigating a case that includes impersonating Marek Suski, obstructing access to his Twitter account, entering new data and removing the password. “Filing a criminal report by Marek Suski, as well as the findings so far in the course of the investigation, have not indicated that classified information may have been disclosed,” said the spokeswoman for the prosecutor’s office Beata Galas.
After the cyberattack on Suski’s account, other members of the special committee described similar attempts to hack into their accounts. “I believe that the matter needs to be looked into, as a special committee we have plans to talk about cybersecurity,” said Marek Biernacki, MP.
According to our sources in secret services, posting fake entries on hijacked social media accounts proves that the hackers had already obtained everything they wanted from the victim. “The milk has been spilt. And the carelessness of politicians, MPs and members of the government regarding digital security is incomprehensible. The amount of sensitive information in unsecured accounts is embarrassing. This data, which could have been already intercepted, could be a critical problem,” we learn from one of our sources in the secret services.
One can expect that the seized email accounts, now laying dormant, can be used for subsequent operations. “Let’s imagine that 30-40 such hacked accounts are suddenly used in the election campaign. This would create a last-minute shitstorm, which would be unmanageable,” says one of our sources in the services.
Moreover, if the owner of a hacked account is unaware that an attack has occurred and their mail has been hijacked (and possibly the entire device), nothing prevents cybercriminals from reading the mail exchange and sending messages – on behalf of a minister, MP, or an influential analyst. And afterwards, they can cover up their activity and delete the emails that have been sent.
8.
Who is (not) afraid of the ghost criminals
Who protects the most important people in Poland against online attacks? In theory, the three-headed dragon responsible for cybersecurity is called the Computer Security Incident Response Team and includes NASK (Scientific and Academic Computer Network at the National Research Institute), GOV (run by the Internal Security Agency or ABW) and the Ministry of National Defence, as well as what remains of the digitisation department transferred few months ago to the Prime Minister’s Chancellery.
How does it work in practice? Our source: “The Internal Security Agency doesn’t want to have to deal with this. Military Counterintelligence Service? No comments.”
We asked the ABW spokesperson whether the series of cyberattacks on politicians is part of a disinformation campaign. We wanted to know who and how reacts in situations when a member of the government has fallen victim to a hacking attack and his social media account or email account has been hijacked.
“The Internal Security Agency has nothing to say in this regard,” the ABW spokesperson said.
When asked whether the prosecutor’s office is carrying out proceedings filed by ABW or other services that result from cyberattacks on politicians, the Warsaw prosecutor’s office sent a brief reply: “No proceedings have been found to meet the criterion included in the question.”
We send similar questions to the Prime Minister’s Chancellery. “Over the past twelve months, several dozen attacks have been detected against private email accounts and social networking sites used by public officials. The exact scale of these attacks is unknown, as not all of them have been reported by people who fell victim,” the Department for Promotion of Digital Policy at the Prime Minister’s Chancellery has written. “Proceedings, after the individuals reported they have fallen victim to cyberattacks, are conducted by law enforcement agencies – the prosecutor’s office and the police. The Prime Minister’s Chancellery has no confirmed information about the sources of attacks on politicians”.
According to our sources, such a large and long-term operation should be viewed as a critical incident. However, despite several meetings between the Internal Security Agency, the Prime Minister’s Chancellery and Government Security Center (RCB), it has not been treated as a major threat.

An excerpt from illustrated guide for MPs that explains how to stay safe online. Source: https://www.gov.pl/
Instead, in November 2020, the government plenipotentiary for cybersecurity, Marek Zagórski (former minister of the now-defunct Ministry of Digitisation), sent a letter to the Speaker of the Sejm addressed to the parliamentary caucus, in which he informed that email address was created to handle reports on phishing attacks. The Prime Minister’s Chancellery has also prepared an illustrated guide for MPs that explains how to stay safe online.
9.
Official accounts full of spam
We asked several MPs about the guide but none of them has seen it.
“The MPs don’t give a damn, as there have been discussions about the security of devices that they use to log into remote parliamentary sessions… Nobody can influence the cybersecurity of MPs, this is a tragedy that can be expressed as a sequence of facepalms,” argues a source who deals with this subject.
The Sejm Chancellery claims that it does organise cybersecurity training. Still, it excludes those MPs who are serving another term in parliament.
IT specialists from the Sejm Chancellery have remote control over the tablets MPs received from the state – they can update the software and send notifications directly to MPs. “The Chancellery does not take part in the activities of MPs that involve their social media accounts. MPs do it on their own and it is their responsibility,” the Sejm’s Information Centre has stressed.
On 17 November 2020, two days before the sensational attack on Duszek, Janusz Korwin-Mikke along with three other members of Konfederacja (Krzysztof Tuduj, Krzysztof Bosak and Michał Urbaniak) sent an MP’s question about the attacks on MPs’ email accounts and claim they received “several thousand unwanted messages and communications that originated from several hundred or even thousand fake online accounts and third parties such as companies and institutions.”
Janusz Korwin-Mikke, one of Konfederacja leaders, has long enjoyed a presence in pro-Russian media such as Sputnik and his public addresses are in line with the Kremlin’s narrative. In 2014, in an interview with Ria Novosti he said that “the annexation of Crimea is completely natural” and encouraged Poland to recognise it. Several months later, he flew to Crimea via Moscow.
Perhaps that is why Konfederacja MPs are looking for the sources of the operation elsewhere, not over the eastern border: “Are the authorities responsible for the state’s internal security and the protection of public order and the protection of Polish MPs investigating or examining the attack as a possible attempt to destabilise the political situation in Poland and to undermine the constitutional order given the popularly of the slogan ‘this is war’,” the Konfederacja representatives ask.
The slogans became popular during the women protests after the Constitutional Tribunal ruling on abortion, which have continued since late October 2020. Two weeks earlier, MP Borowiak’s hacked and seized Twitter account had been used to spread vulgarities aimed at women taking part in the protest action.
Jan Grabiec, a Civic Coalition MP, chairman of the parliamentary committee for digitisation, innovation and new technologies, has said that shortly after the first phishing attacks the MPs had received notifications on their tablets warning them to be careful online.
“Have you heard about the cybersecurity guide?” we ask.
“Some guides might have been sent to the caucus, but to be honest, I do not know exactly,” he says. When we ask him to authorise his statements for the report, he asks us to send it to his private email account. He explains that it is impossible to use the official email as it is full of spam.
Julia Dauksza from Reporters’ Foundation (Poland) and Sarunas Cerniauskas from Siena.lt (Lithuania) also contributed to this report.
Anna Gielewska is co-founder and editor-in-chief of VSquare and co-founder of Polish investigative outlet FRONTSTORY.PL. She is also vice-chairwoman of Fundacja Reporterów (Reporters Foundation). A journalist specializing in investigating organized disinformation and propaganda, Gielewska was the John S. Knight Fellow at Stanford University (2019/20) and has been shortlisted for the Grand Press Award (2015, 2021, 2022) and the Daphne Caruana Galizia Award (2021, 2023). She was the recipient of the Novinarska Cena in 2022.
Konrad Szczygieł is an investigative journalist at FRONTSTORY.PL. Previously, he was a reporter at Superwizjer TVN and OKO.Press. Since 2016, he has worked with Fundacja Reporterów (Reporters Foundation). He was shortlisted for a Grand Press award (2016, 2021) and an Andrzej Woyciechowski award (2021). He is based in Warsaw.








